1. Brief Overview of the OWASP Top 10:
- The OWASP Top 10 is a standard awareness document for developers and web application security. It represents a broad consensus about the most critical security risks to web applications.
- The list is compiled by security experts worldwide and is updated regularly to reflect the evolving landscape of security threats.
- The OWASP Top 10 aims to raise awareness about the importance of web application security and provide guidance on mitigating the most prevalent vulnerabilities.
A02:2021 – Cryptographic Failures: This category of OWASP Top Ten focuses on failures related to cryptography, which often lead to sensitive data exposure or system compromise. It was previously known as Sensitive Data Exposure but has been updated to emphasize the root causes rather than the symptoms.
Cryptographic failures occur when sensitive data is not properly protected due to weaknesses in encryption algorithms, key management, transmission methods, and other cryptographic practices.
2. Understanding Cryptographic Failures
Cryptographic Failures: These are vulnerabilities that arise from improper implementation or use of cryptographic systems, leading to the exposure of sensitive data or system compromise.
How They Occur:
- Using weak or deprecated cryptographic algorithms that can be easily broken by attackers.
- Poor key management practices, such as insecure storage, generation, and handling of cryptographic keys.
- Transmitting sensitive data over unencrypted or insecure channels.
- Incorrect implementation of cryptographic protocols, such as using predictable initialization vectors (IVs) or failing to use them altogether.
- Failing to encrypt sensitive data at rest or in transit, leaving it vulnerable to interception and unauthorized access.
Impact of Cryptographic Failures on Applications and Users
Impact on Applications:
- Compromise of sensitive data such as user credentials, financial information, and personal data.
- Potential for attackers to gain unauthorized access to systems and data.
- Legal and regulatory consequences for failing to protect sensitive data (e.g., GDPR fines).
Impact on Users:
- Increased risk of identity theft and fraud.
- Loss of trust in the affected application or service provider.
- Exposure of personal and financial information.
3. Common Cryptographic Failures
Weak or Deprecated Algorithms:
- Definition: Using outdated or insecure cryptographic algorithms that no longer provide adequate security.
- Example: Using MD5 or SHA-1 for hashing passwords, which are vulnerable to collision attacks.
Poor Key Management:
- Definition: Insecure handling, generation, and storage of cryptographic keys, which can lead to unauthorized access.
- Example: Storing encryption keys in plaintext on the same server as the encrypted data.
Insecure Transmission:
- Definition: Sending sensitive data over unencrypted channels, making it susceptible to interception by attackers.
- Example: Transmitting user credentials over HTTP instead of HTTPS.
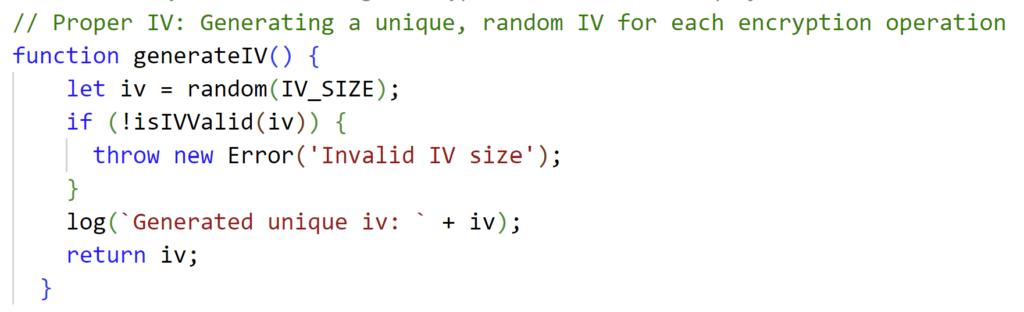
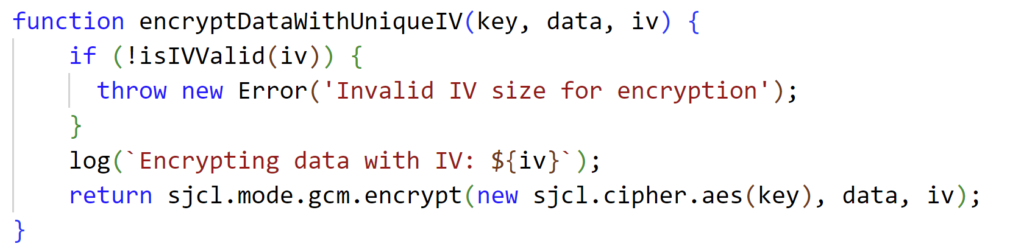
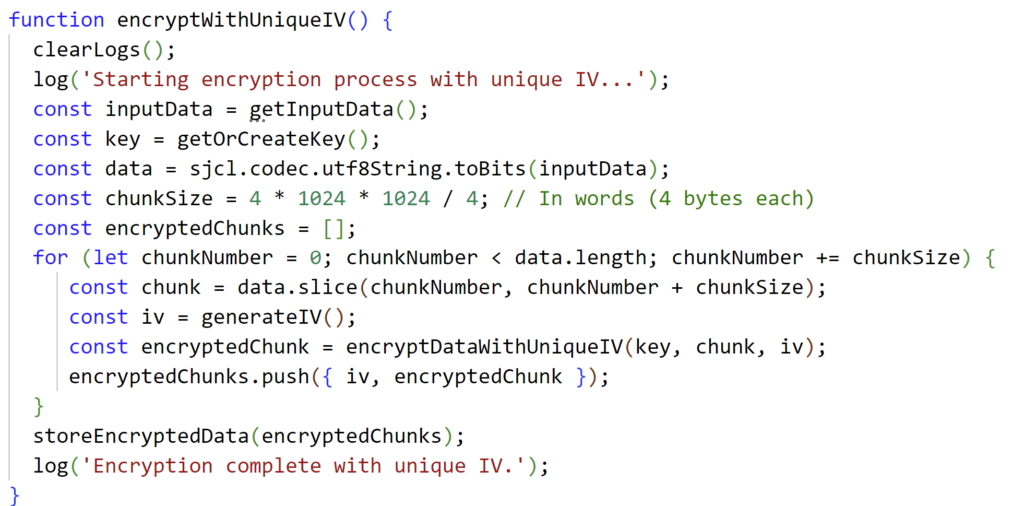
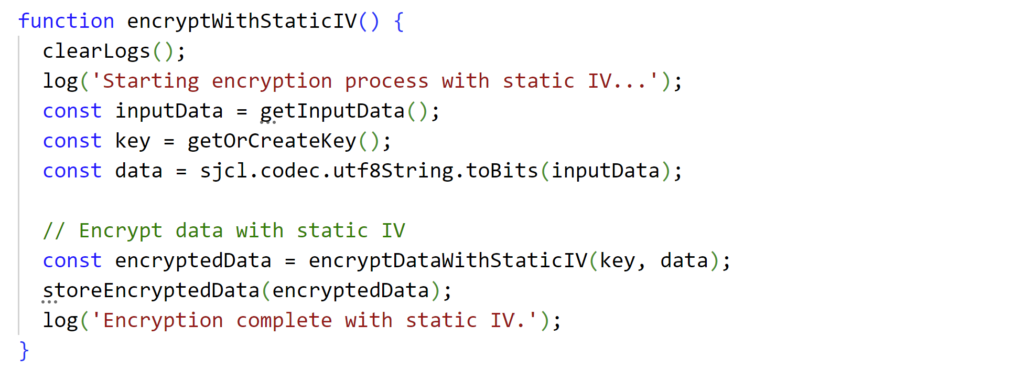
Improper Initialization Vectors (IVs):
- Definition: Using predictable IVs or failing to use them, which weakens the security of encryption schemes.
- Example: Using a static IV for all encryption operations, allowing attackers to recognize patterns in encrypted data.
Lack of Encryption:
- Definition: Storing or transmitting sensitive data without encryption, leaving it exposed to unauthorized access.
- Example: Storing user passwords in plaintext in a database.
4. Real-world Examples of Cryptographic Failures
Example 1: Heartbleed Vulnerability (2014):
- Description: A critical vulnerability in the OpenSSL cryptographic software library allowed attackers to read sensitive data from the memory of servers, including private keys and user data.
- Consequence: Exposure of sensitive information from millions of servers, leading to widespread security breaches.
Example 2: Equifax Data Breach (2017):
- Description: The breach was partially due to weak encryption practices and poor key management. Attackers exploited these weaknesses to access sensitive data, including Social Security numbers and credit card information.
- Consequence: Compromise of personal data for over 147 million people, resulting in significant financial and reputational damage to Equifax.
Example 3: Adobe Data Breach (2013):
- Description: Attackers accessed Adobe’s systems and stole encrypted passwords and password hints. The encryption used was weak, and many passwords were easily cracked.
- Consequence: Exposure of over 38 million user accounts, including customer IDs and encrypted passwords.
5. Best Practices for Secure Cryptography
- Use Strong Encryption Algorithms: Ensure the use of secure, industry-standard algorithms (e.g., AES-256).
- Secure Key Management: Implement secure methods for generating, storing, and managing cryptographic keys.
- Encrypt Data in Transit and at Rest: Use TLS/SSL for data transmission and encrypt sensitive data stored in databases.
- Proper IV Usage: Ensure proper use of IVs with encryption algorithms to enhance security.
- Regular Audits and Updates: Regularly audit and update cryptographic implementations to adhere to the latest security standards.
6. Improper use of static IVs for all encryption operations
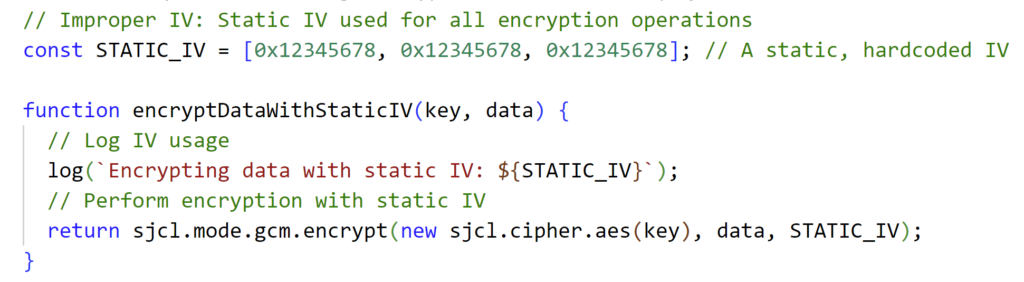
7. Proper use of unique and random IVs for all encryption operations