💡 Stealing human information is known as social engineering. As it does not require interaction with target systems or networks, it is considered a non-technicalattack. Social Engineering is seen as convincing the target to reveal and share information. The process may be executed through physical interaction with the target or by convincing the target to part with information using any social media platform. This technique is much easier than others because people are careless and often unawareof the importanceand value of the information they possess.
Vulnerabilities Leading to Social Engineering Attacks
💡 “Trust” is a major vulnerability that can be used for social engineering. Humanstrusteach other anddonot secure their credentials from their close ones, which can lead to an attack. A third person may shoulder surf for information or reveal information from a second person to a third.
Organizations unaware of social engineering attacks, their impact, and countermeasures are also vulnerable to becoming victims of these attacks. Insufficient training programs and employee knowledge createsa vulnerability in the security system’s ability to defend against social engineering attacks. Every organization must train its employees to be aware of social engineering.
Each organization must also secure its infrastructure physically. Employeeswith different levels of authority should be restricted from performing their tasks. An employee prevented from accessing specific departments, such as the finance department, should have their access restricted to their department. Employees who move freely between departments might perform social engineering by dumpster diving or shoulder surfing.
Another vulnerability is a lack of privacy and security policies. A strong security policy must be in place to prevent an employee from impersonating to be another user. Privacy between unauthorized people, clients, and employees must be maintained to keepthings secure from unauthorized access ortheft.
Phases of a Social Engineering Attack
Social Engineering Attacks are not complicated, nor do they require strong technical knowledge—an intruder may be a non-technical individual, as we defined earlier. Stealing information from other people is an act. However, the following steps are used to carry out social engineering attacks:
💡 Attacks based on social engineering use human nature to want to help others, trust others, and be afraid of getting into trouble. A social engineer with patience and determination can exploit this nature. Some of the most common attack types or methods that social engineers can use to target their victims include scareware, phishing, pretexting, baiting, and tailgating.
Research
The research phase contains data about a target organization that must be gathered. It could be collected by dumpster diving,looking at an organization’s website, finding information online, asking employees for information, etc.
Select Target
In choosing a target phase, an attacker chooses the target among different employees of an organization. A frustrated target is preferable, as extracting information from such a person is usuallyeasier.
Relationship
The Relationship phase consists of creating a relationshipwith the target so that the target cannot identify the attacker’s real intentions. The target should completely trust the attacker.
Exploit
In this stage, the attacker exploits the relationship by collectingsensitive information such as usernames, passwords, network information, etc.
Social Engineering Techniques
There are a variety of techniques for carrying out social engineering attacks, which are categorized as follows:
Human-based Social Engineering
One-on-one interactions with the target are part of human-based social engineering. A social engineer gathers sensitive information by tricking the target, ensuring trust, and taking advantage of habits, behavior, and moral obligations.
1. Impersonation
Impersonating is a human-based social engineering technique. Pretending to be someone or something is known as impersonation. In this context, impersonation refers to either pretending to be a legitimate user or an authorized individual. This impersonation can occur face-to-face or through a communication channel, including email or telephone.When an attacker has sufficient personal information about an authorized person, they can commit personal impersonation, alsoknown as identity theft. By providing the legitimate user’s personal information, either collected or stolen, an attacker assumes the identity of a legitimate user. Impersonating a technical support agent and asking for credentialsis another impersonation method for gathering information.
2. Eavesdropping and Shoulder Surfing
Eavesdropping is a technique in which an attacker gathersinformation by covertly listening toa conversation. It also includes reading or accessing any source of information without being noticed.Shoulder Surfing is defined in the “Footprinting”section in this workbook. Shoulder Surfing, in short, is a method of gathering information by standing behind a target when interacting with sensitiveinformation.
3. Dumpster Diving
Dumpster Diving is the process of looking fortreasure in the trash. This technique is old but still effective. It includes accessing the target’s trash, such as printer trash, their user desk, or the company’s trash, to find phone bills, contact information, financial information, source codes, and other helpful material.
4. Reverse Social Engineering
A Reverse Social Engineering attack requires the interactionof the attacker and the victim, where an attackerconvinces the target they havea problem or might have an issue in the future. If the victim is convinced, they will provide the attacker with the information requested. The following steps are used to perform reverse social engineering:
a. An attacker harms the target system or identifies the known vulnerability.
b. An attacker advertises himself as an authorized person to solve that problem.
c. An attacker gains the target’s trust and obtains access to sensitive information.
d. Upon successful reverse social engineering, the usermay often approach the attacker for help.
5. Piggybacking and Tailgating
Piggybacking and Tailgating aresimilar techniques. Piggybacking is a technique in which an unauthorized person waits for an authorized person to gain entry to a restrictedarea, whereas tailgating is a technique in which, by following the authorized person, an unauthorized person gains access to a restricted area. Using fake IDs and closely following the target while crossing checkpoints makes tailgating simple.
Computer-based Social Engineering
There are various ways of performing PC-based social engineering. The most popular methods are pop-up windows requiring login credentials, Internet messaging, and emails such as Hoax Letters, Chain Letters, and Spam.
1. Phishing
The process of sending a fake email to a target host and looking like an authorized email that appears to be processed is known as phishing. The recipient is enticed to provide information when they click on the link. Typically, users are redirected to fake web pages that resemble an official website. Because of the resemblance, the userprovidessensitive information to a fake website, believing it is official.
2. Spear Phishing
Spear phishing is a type of phishing that focuses on a single person. It is an individual-specific phishing attack. Spear phishing produces a higher reaction rate than a random phishing attack.
⚠️ The attacker may attempt to duplicate the third party’s email address and use their research to assume the identity of a third-party employee, possibly someone they believe their victim knows. They might even try to access the email account of the third party.
Mobile-based Social Engineering
1. Publishing Malicious Apps
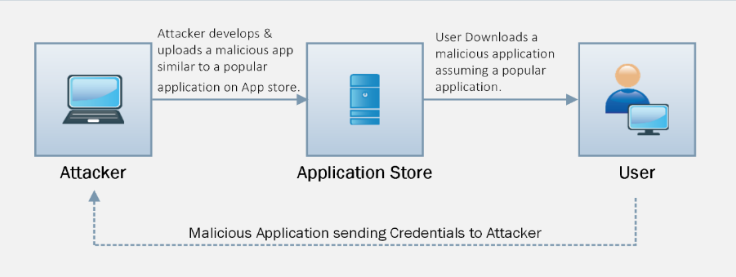
Mobile-based Social Engineering is the technique of publishing malicious applications on an application store. Being available on an official application store increases the chances of the application being downloaded on a large scale. These malicious applications are normally replicas or similar copies of a popular application. For example, attackers can develop malicious applications for Facebook. Instead of downloading an official application, a usermay accidentallyor intentionally download this third-party malicious application. When the usersignsin, this malicious application will send the login credentials to a remote server controlled by the attacker.
2. Repackaging Legitimate Apps
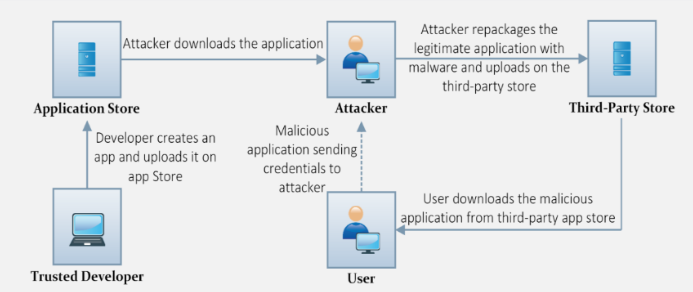
Another technique of mobile-based social engineering involves an attacker repackaging a legitimate application with malware. The attacker initially downloadsa popular and in-demand application, such as games or antivirus, from an application store. The attacker then repackagesthe application with malware and uploadsit toa third-party store. A usermay not beaware of the availabilityof the application on the official application store,or they may get a link for downloading a paid application for free. Instead of downloading an official application from a trusted store, the useraccidentallyor intentionally downloadsthe repackaged application from a third-partystore. When they signin, the malicious application sends the login credentials to a remote server controlled by the attacker.
3. Fake Security Apps
An attacker may develop a fake security application similar to the above techniques. This security application can then be downloaded by a pop-up window when usersbrowse the infected website.
Insider Attack
Social Engineering does not just refer to a third person gathering data aboutyour organization. It may be an insider, an organization employee with or without privileges, or spying onyour organization for malicious intentions.Insiderattacks arethose conducted by these insiders, who may be supported by a competitor of the organization hoping to obtain secrets and other sensitive information.As well as spying, another intention may be getting revenge. A disgruntled employee may compromise confidential and sensitiveinformation. Such an employee may be unhappy withmanagement, bein trouble, or face demotion or termination of employment.
Hoaxes
It is a type of threat where an organization is warned of a particular problem and then asked for money to solve or remove it. Threats of this kind can be sent via tweets, Facebook posts, or email; theobjective is to deceive others and earn money.
Watering Hole Attacks
These attacks are carried out when the security inside an organization is extremely strong; attackers cannot get inside the network and attack the security system by using threats. In this situation, the threat actor attacks what the insiders visit rather than attacking the insider. To do this, the attacker needs to know which sites the insiders commonly visit, and they can then attack the organization by attacking the third party. For the defense and security of the system, there should bemultiple ways of identifying these attacks and stopping them from penetrating the network.
Impersonation on Social Networking Sites
Social Engineering Through Impersonation on Social Networking Sites
Impersonation on Social Networking Sites for Social Engineering Impersonation on social networking sites is very common, simple, and interesting. The gathered information may includethe full name, a recent profile picture, date of birth, residential address, email address, contact details, professional details, educational details, etc. After gathering the information about a target, the attacker creates an account that is the same as that person’s account. This fake account is then introduced to friends and groups joined by the target. Usually,people do not question a friend request; if they do and find accurate information,they accept the request.

Once an attacker joins the social media group where a user shares their personal and organizational information, they will get updates from groups. An attackercan also communicate withthe target’s friends, convincing them to reveal information.
Risks of Social Networking to Corporate Networks
A corporate website is more secure than a social networking site. The authentication, identification, andauthorization of employees accessing resources on these sites are different. For example, logging into a bank account through a website and a social media account has different levels of security. Sensitive information is not stored on social networking sites; consequently, they use ordinary authentication. Social networking’s authentication vulnerability is its major weakness. An attacker can easily alter the security authentication and make a fake account to gain access to information. Employeesmay be careless about sensitive information when communicating on social networking sites. They may, therefore, accidentallyor intentionally reveal information that can be useful to the attacker they are communicating with or a third person monitoring the conversation. A strongpolicy against data leakage is required.
Types of Social Engineering
There are various types ofsocial engineering that provide some basic fundamental characteristics. The following are the most typical types of social engineering:
Bating
The attacker distributes hardware infected with a virus or malicious software to unsuspecting individuals. Malware attacks a computer when the hardware, like a CD-ROM, USB, or flash drive, is inserted into the computer.
💡 For example, A criminal could leave a typical virus-infected USB, like a flash drive, in a public place like a washroom, elevator, or packing area,etc., where they are easily visible to vulnerable individuals. The bait frequently has an appealing appearance resembling a company label or a colorfully branded pet.
Scareware
Scareware is malware that uses social engineering to get people to buy unwanted software by making them feel scared and anxious. Scareware is part of a class of malware that includes rogue security software, ransomware, and other scam software that makespeople think their computer has a virus and then tells them to download and payfor fake antivirus software to get rid of it.
💡 For example, according to Google research, scareware was using some of Google’s servers to check for internet connectivity. The company has displayed a warning in the search results of users whose computers appear to be infected, as the data suggested that up to one million were infected with scareware.
Smart Fortress is another example of scareware. Here, the victim is frightened and asked to pay for professional services on this website, which suggests that their computer is infected with many viruses.
Pretexting
Pretexting is a form of social engineering in which plausible scenarios, or pretexts, are created to convince victims to share sensitive and valuable data. It could be a password, information about your credit card, personally identifiable information, confidential data, or anything else that could be used for fraud, like identity theft.
💡 For example, a scammer might call victims pretending to be from a credit card company and request confirmation of their account information. If the victim trusts them, they might hand over their payment information without realizing that cybercriminals have access to it.
Phishing
Phishing is the process by which an attacker sends fake emails claiming to be from Google,Facebook, or another legitimate company. For the attacker to gain access to the target’s computer, the victims must provide financial and personal information.
💡 For example, a user of an online service may receive an email notifying them of a potential policy violation that may require immediate correction, such as changing their password. It could be a link to a malicious website resembling a legitimate website and asking users to change their login information. The information is given to the hackers after the modification and may be used to commit fraud activities.
Spear Phishing
It is a more targeted form of phishing in which the hacker targets a specific individual or company. To make the scams less obvious, the attacker customizes the messages based onthe victims’ features, occupations, phone numbers, and email addresses. This kind of social engineering requires a lot of effort from the attacker, which makes it hard to detect. If executed well, it has a biggestsuccess rate.
Fake websites are an example of spear phishing. A cybercriminal will design a carefully worded phishing email with a link to a fake version of a popular website. The victim is tricked into entering their account credentials by the website, which imitates the original site’s layout.
Vishing
The only difference between this and phishing is that audio is used. The “scam call” is the social engineering attack used most frequently, where it is possible to fake caller identification numbers.Government Representative is an example of vishing. The caller claims to approach on behalf of the government and calls to confirm individual recognizable identifications details. The caller may threaten to halt social security payments or tax refunds if the victim does not provide the information necessary to verify their account and identity.
Whale phishing
Whale Phishing targets high-profile victims. Celebrities, politicians, and high-ranking businesspeople are examples of this. The attacker usually tries to get these well-known targets to give their personal information or business credentials. Social engineering is typically used in whaling attacks to trick the victim into believing the deception.
How to recognize a phishing attack
A few additional signs of a phishing attempt include:
- The email’s offer appears too good to be true. It could declare that you have won an expensive prize, the lottery, or something else.
- You are aware of the sender, but you have not spoken to them. Even if you know the sender’s name, be suspicious if you do not normally communicate with them, especially if the content of the email has nothing to do with your job duties. The same applies if you are sent an email to people you do not know, such as a group of coworkers from different business units.
- It sounds like a scary message. If the email urges you to click and “act now” before your account is closed, beware if it contains alarmist or charged language. Remember that responsible businesses never ask for personal information over the Internet.
- Unexpected or unusual attachments are in the message. Malware, ransomware, or another online threat might be in these attachments.
- There are links in the message that do not look quite right. Do not take any embedded hyperlinks at face value, even if your spider-sense is not tingling about any of the above. Instead, hover your cursor over the link to see the actual URL. When looking at a website that otherwise appears authentic, be alert for subtle misspellings because these are signs of fraud. Instead of clicking on the embedded link, typing in the URL yourself is always preferable.
Examples of phishing attempts
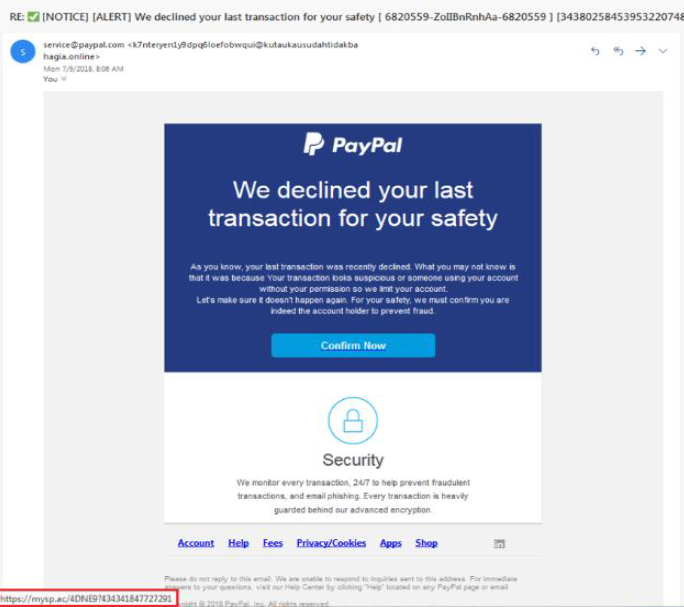
Here is an example of a phishing scam that tries to trick the recipient into clicking on a PayPal notification that says, “Confirm Now.” The real URL destination is shown in the red rectangle when the mouse hovers over the button.
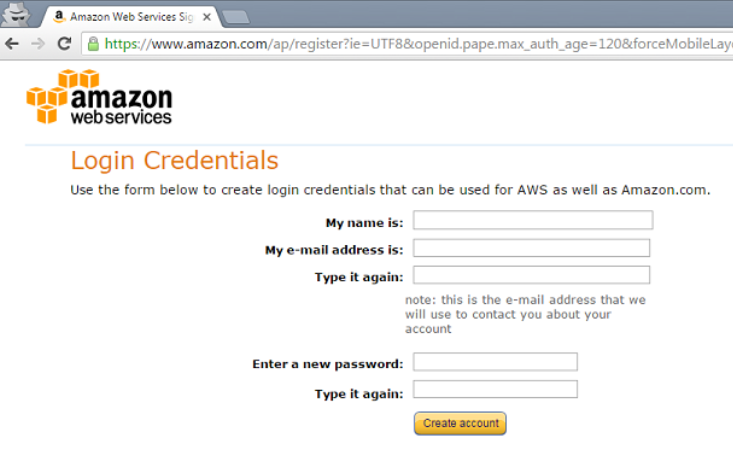
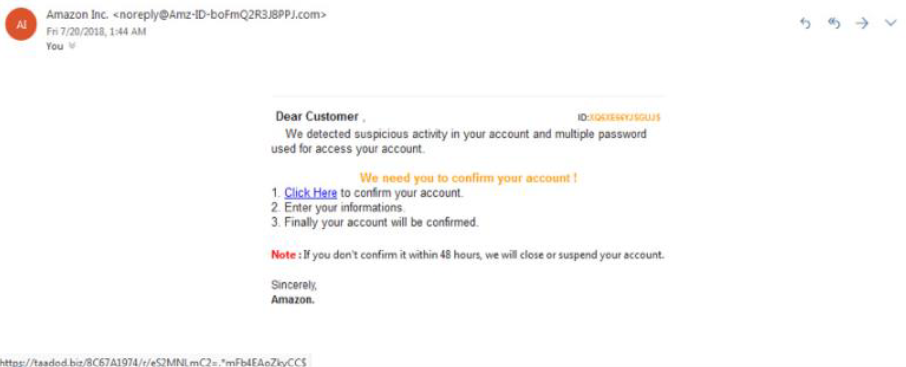
Another image of a phishing attack, this one claiming to be from Amazon, can be found here. Take note of the threat to close the account if nothing is done within 48 hours.
By clicking the link, you are taken to this form, where you are asked to provide the information the phisher needs to steal your valuable details: